I Suck At CTFs: Breakout - Empire
Well - I suck at CTFs. Maybe I just don’t have the CTF mindset, but here’s to trying to do a challenge a day until I start to like it or can them without a walkthrough =p
tl;dr
dcode.fr
CTF-ism tool when dealing with cipher stuff. You can use the site to identify the type of cipher being used and crack it
Real world application: Can use it to crack ciphers but there’s a privacy issue, how do I know it’s not saved or something?
enum4linux $IP
Useful if nmap identifies smb or samba ports open
getcap $BINARY
Built-in command to identify the capabilities that a binary has.
Interesting ones are:
cap_dac_read_searchRead any file, bypassing file permissions
cap_net_rawSend raw packets
ping(usually harmless)
cap_setuidSet UID to 0 (root)
cap_sys_adminDo almost anything (like root) Dangerous if found
find $DIR -name “.*” 2>/dev/null
looks in $DIR for interesting files
most useful in specific directories vs the entire filesystem
./tar -cf - $FILE | tar -xf -
in this box the local tar binary had different getcap than the systemwide tar
created the tarball (tar file) as root and then extracted it without permissions so regular users can read it
MITRE ATT&CK Technique IDs:
T1595.002 – Active Scanning: Network Scanning
T1597.001 – Search Open Websites/Domains: Code Repositories
T1552.001 – Unsecured Credentials: Credentials in Files
T1110.002 – Brute Force: Password Cracking
T1087.001 – Account Discovery: Local Account
T1083 – File and Directory Discovery
T1548.001 – Abuse Elevation Control Mechanism: Setuid and Setgid
T1552.001 – Unsecured Credentials: Credentials in Files
Start off with the typical NMAP scan
Received 80, 139, 445, 10000, and 20000
10000 and 20000 not shown
T1595.002 – Active Scanning: Network Scanning
Go to the browser and head to IP:80
Hitting the web page with the Source Code and scrolling down we see this
T1597.001 – Search Open Websites/Domains: Code Repositories
T1552.001 – Unsecured Credentials: Credentials in Files
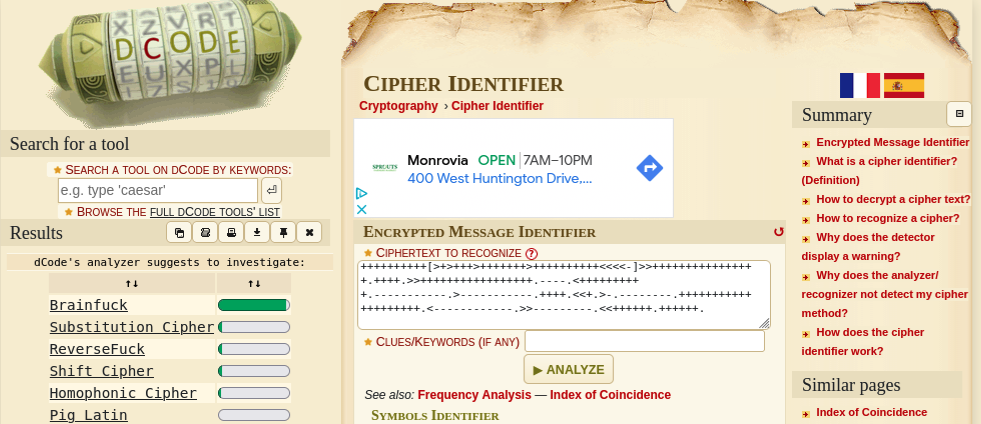
Head to dcode.fr
You can use the CIPHERTEXT TO RECOGNIZE function
This shows a high confidence of the Brainfuck cipher
That gives us a password to use
T1110.002 – Brute Force: Password Cracking (this is the most fitting for decrypting of captured cipher texts)
We don’t have a username, remembering that we saw 139 and 445
Use enum4linux to enumerate samba for a username
We find the cyber user
So now we have a username and a password
T1087.001 – Account Discovery: Local Account
Hit the IP:10000 in the web browser
Username and password doesn’t work there
Head to IP:20000
Username and password works there!
Going through the menu we see Command Shell and we can cat the user.txt
T1083 – File and Directory Discovery
Searching msfconsole we find a lot of different exploits with webmin
Tried all of them and even with a username and password the exploits weren’t successful (I think?)
Back to the VM, using the Command Shell we find the tar binary
Using getcap we can find what capabilities the binary has
T1548.001 – Abuse Elevation Control Mechanism: Setuid and Setgid
getcap is a Linux command used to check which capabilities are assigned to binaries. Capabilities allow a binary to perform specific privileged actions without needing full root privileges (unlike SUID).
🧭 Summary:
Command:
getcap -r / 2>/dev/nullPurpose: Find binaries that may be used for privilege escalation without SUID
🔥 Interesting Capabilities for Privesc:
cap_dac_read_searchRead any file, bypassing file permissions
cap_net_rawSend raw packets
ping(usually harmless)
cap_setuidSet UID to 0 (root)
cap_sys_adminDo almost anything (like root) Dangerous if found
With the tar binary with those capabilities, CTF-ism says there’s gotta be a file that we need to read that we can’t read
find /var/ -name “.*” 2>/dev/null gives us a hidden .old_pass.bak
use the tar binary in the cyber directory to read the .bak file
./tar -cf - /var/backups/.old_pass.bak | tar -xf -
./tar -cf : this creates the “tarball”
- : this first argument position tells where to create the tarball, the hyphen just says to make output it STDOUT
/var/backups/.old_pass.bak : this is the file we want to read
| tar -xf - : this will take the output of the first tar and the -xf will extract it
It extracts it with the full path so the /var/backups/ directories are there
We can then cat the .bak file
T1552.001 – Unsecured Credentials: Credentials in Files
Now we can use root and log into 10000
This is not shown, but we know the username is root because reading /etc/passwd, root is the only other login-able user
We can then get to Command Shell
With the shell as root we can then read the r00t.txt file