I Suck at CTFs: Breakout - Lupin One
tl;dr
TTP IDs:
T1595.002 – Active Scanning: Network Scanning
T1592.005 – Gather Victim Identity Information: Sensitive Files
T1595.001 – Active Scanning: Web Application Scanning\
T1110.002 – Brute Force: Password Cracking
T1083 – File and Directory Discovery
T1548.003 – Abuse Elevation Control Mechanism: Sudo and Sudo Caching
T1059.006 – Command and Scripting Interpreter: Python
NMAP shows 80 and 22
Check the source code of IP:80
Nothing here
T1595.002 – Active Scanning: Network Scanning
Main webpage
Check robot.txt as a CTF-ism
Navigate to IP/~myfiles
T1592.005 – Gather Victim Identity Information: Sensitive Files
Fake Error 404
More source code encouragement
Trying different filesystem type of locations to see if I find anything.
Nothing else found.
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.0.2.3/FUZZ
Came out with some results with image, manual, javascript
T1595.001 – Active Scanning: Web Application Scanning
Installed jq so i can read the json outputs better
jq -r : take the raw results
‘.results[] : go into the results array
| “\(.status) \(.length) \(.url)”’ : pull out the status length and url. the extra stuff is just syntax for the command
The image, manual, javascript didn’t come up with anything.
Took a dive down the rabbit hole with looking up specific exploits for the server and service. That lead no where as well.
Got a hint from the walkthrough to ffuf with the tilde. So ran the same ffuf command but included the tilde and found ~secret directory.
CTF-isms: 1) username is icex64 2) fasttrack.txt is hint to use this wordlist in the future 3) there is a private key used to ssh hidden somewhere in open directories we need to find
T1595.001 – Active Scanning: Web Application Scanning
Got another hint from a walkthrough to append extensions to the end of my ffuf commands. But in the same light as the tilde, use the period before the document name because it’s supposed to be hidden, like on linux filesystems.
Resulted in finding ~secret/.secret.txt which is a huge text blob that is supposed to be the key
T1595.001 – Active Scanning: Web Application Scanning (same TTP even if looking for hidden files vs hidden directories)
Use fcode to decipher or identify ciphers we see it’s base58.
Decoding that gives us the correct key format.
T1110.002 – Brute Force: Password Cracking
Was able to save the key into a file.
ssh into the server as icex64 we are asked to provide a passkey. Wtf.
Got a hint from a walkthrough to use ssh2john to convert the key into something that john the ripper can crack and provide the passphrase for.
Based on the fasttrack hint file we are able to use that against the key to get P@55w0rd!
T1110.002 – Brute Force: Password Cracking
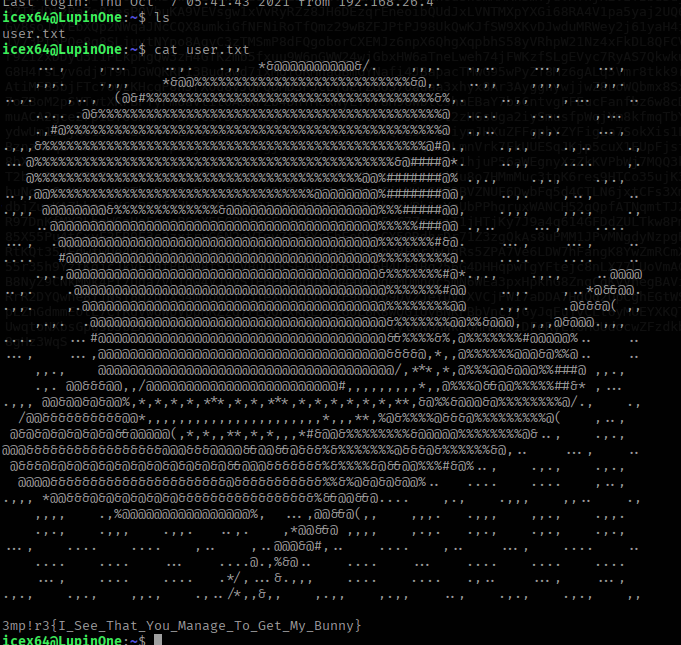
ssh-ing in and using the cracked passphrase brings us to the user.txt file!
Enumerating the box we see that we can log in as arsene and root, as they are other users on the system
Checking the note.txt file we see that there are more “secret” files to look for.
T1083 – File and Directory Discovery
Checking sudo -l we can see that we can run “python3.9 /home/arsene/heist.py” as the user arsene under sudo without issue.
(arsene) NOPASSWD: …python3.9 …heist.py
This means we can run the python file with “sudo -u arsene” without a password
T1548.003 – Abuse Elevation Control Mechanism: Sudo and Sudo Caching
Walkthrough hint told me to cat heist.py and that showed us that the .py script imported a webbrowser module. That’s a hint to look into that library.
Nano-ing that library, we are able to put whatever command we want.
The commented import pty was supposed to be a reverse shell but my nc listener wasn’t picking it up for whatever reason.
I just hardcoded the commands I wanted the os to run with those print statements and I was able to get the arsene user password.
T1059.006 – Command and Scripting Interpreter: Python
ssh into the server as arsene
check sudo -l for what we can run and it shows we can run pip as root without a password
Checked gtfobins for pip and there’s this option to run pip to get a shell.
T1548.003 – Abuse Elevation Control Mechanism: Sudo and Sudo Caching
Typed in those shell commands and for the last line ran sudo -u root pip install $TF and was able to get root shell and print root.txt
changed the password for root to root